Cybersecurity is the practice of protecting systems, networks, and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It is a broad term that encompasses a wide range of security measures, from physical security to information security.
Cybersecurity is important because it protects our personal information, our businesses, and our critical infrastructure. In today’s digital age, our lives are increasingly reliant on technology. We use technology to communicate, to work, to shop, and to entertain ourselves. This reliance on technology makes us vulnerable to cyberattacks.
Cyberattacks can have a devastating impact on individuals, businesses, and governments. They can steal our personal information, our financial information, and our intellectual property. They can disrupt our businesses, causing us to lose money and productivity. And they can even damage our critical infrastructure, such as our power grid and our transportation system.
There are a number of things that we can do to protect ourselves from cyberattacks. We can use strong passwords, keep our software up to date, and be careful about what information we share online. We can also install security software on our computers and mobile devices. And we can be aware of the latest cybersecurity threats and how to protect ourselves from them.
Cybersecurity is a complex and ever-evolving field. But by taking some simple steps, we can help to protect ourselves from cyberattacks and keep our information safe.
Here are some of the most common cybersecurity threats:
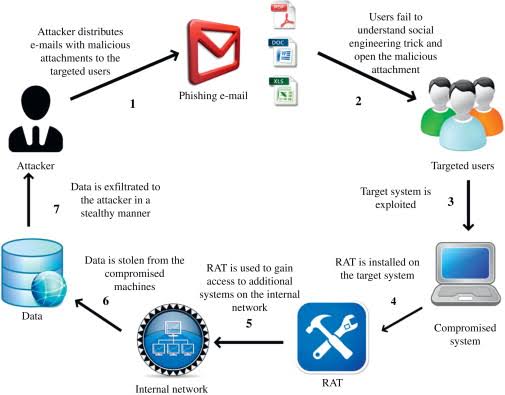
- Phishing: Phishing is a type of cyberattack in which attackers send fraudulent emails that appear to be from legitimate sources. The goal of phishing is to trick the recipient into clicking on a malicious link or providing personal information.
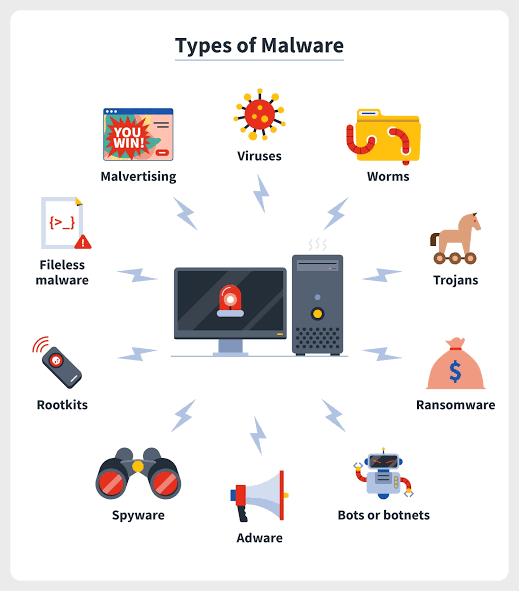
- Malware: Malware is a type of software that is designed to damage or disable computers and computer systems. Malware can be spread through email attachments, malicious websites, and USB drives.

- Ransomware: Ransomware is a type of malware that encrypts a victim’s files and demands a ransom payment in order to decrypt them. Ransomware attacks are becoming increasingly common, and the ransom payments can be very high.

- Data breaches: A data breach is an incident in which sensitive data is exposed to unauthorized individuals. Data breaches can occur through a variety of means, including hacking, phishing, and employee negligence.
Here are some of the best practices for cybersecurity:
- Use strong passwords: Passwords should be at least 12 characters long and include a mix of upper and lowercase letters, numbers, and symbols.
- Keep your software up to date: Software updates often include security patches that can help to protect your devices from cyberattacks.
- Be careful about what information you share online: Only share personal information with people you trust.
- Install security software: Security software can help to protect your devices from malware and other cyberattacks.
- Be aware of the latest cybersecurity threats: Stay up-to-date on the latest cybersecurity threats and how to protect yourself from them.
By following these best practices, you can help to protect yourself from cyberattacks and keep your information safe.

